TOP 10 Secure Coding Best Practices Results at 10Bestify.com
-
Secure Coding Best Practices A Complete Guide - 2020 Edition
Is the network connection required as part of another contract with your organization? Do you control inter-zone communication? Who are the users of the cloud systems? What parameters should you measure? What do you need to change to make sure this mistake never happens again? Defining, designing, creating, and implementing a process to solve a challenge or meet an objective is the most valuable role… In EVERY group, company, organization and department.Unless you are talking a one-time, single-use project, there should be a process. Whether that process is managed and implemented by humans, AI, or a combination of the two, it needs to be designed by someone with a complex enough perspective to ask the right questions. Someone capable of asking the right questions and step back and ... [Read More] Secure Coding Best Practices
- ASIN: B07YYV2YZW
- ASIN: B07YYV2YZW
- Manufacturer: 5STARCooks
-
Writing Secure Code, Second Edition (Developer Best Practices)
Keep black-hat hackers at bay with the tips and techniques in this entertaining, eye-opening book! Developers will learn how to padlock their applications throughout the entire development process—from designing secure applications to writing robust code that can withstand repeated attacks to testing applications for security flaws. Easily digested chapters reveal proven principles, strategies, and coding techniques. The authors—two battle-scarred veterans who have solved some of the industry’s toughest security problems—provide sample code in several languages. This edition includes updated information about threat modeling, designing a security process, international issues, file-system issues, adding privacy to applications, and performing security code reviews. It also includes... [Read More] Secure Coding Best Practices
- ASIN: 0735617228
- UPC: 790145172280
- ASIN: 0735617228
- ISBN: 0735617228
- Brand: Microsoft Press
- Manufacturer: Microsoft Press
-
Java Coding Guidelines: 75 Recommendations for Reliable and Secure Programs (SEI Series in Software Engineering)
“A must-read for all Java developers. . . . Every developer has a responsibility to author code that is free of significant security vulnerabilities. This book provides realistic guidance to help Java developers implement desired functionality with security, reliability, and maintainability goals in mind.” –Mary Ann Davidson, Chief Security Officer, Oracle Corporation Organizations worldwide rely on Java code to perform mission-critical tasks, and therefore that code must be reliable, robust, fast, maintainable, and secure. Java™ Coding Guidelines brings together expert guidelines, recommendations, and code examples to help you meet these demands. Written by the same team that brought you The CERT® Oracle ® Secure Coding Standard for Java™, this guide extends ... [Read More] Secure Coding Best Practices
- ASIN: 032193315X
- ASIN: 032193315X
- ISBN: 032193315X
- Brand: Brand: Addison-Wesley Professional
- Manufacturer: Addison-Wesley Professional
-
Distributed Source Coding: Theory and Practice
Distributed source coding is one of the key enablers for efficient cooperative communication. The potential applications range from wireless sensor networks, ad-hoc networks, and surveillance networks, to robust low-complexity video coding, stereo/Multiview video coding, HDTV, hyper-spectral and multispectral imaging, and biometrics. The book is divided into three sections: theory, algorithms, and applications. Part one covers the background of information theory with an emphasis on DSC; part two discusses designs of algorithmic solutions for DSC problems, covering the three most important DSC problems: Slepian-Wolf, Wyner-Ziv, and MT source coding; and part three is dedicated to a variety of potential DSC applications. Key features: Clear explanation of distributed source coding theory a... [Read More] Secure Coding Best Practices
- ASIN: 0470688998
- ASIN: 0470688998
- ISBN: 0470688998
- Brand: Wiley
- Manufacturer: Wiley
-
Professional WordPress: Design and Development
The highest rated WordPress development and design book on the market is back with an all new third edition. Professional WordPress is the only WordPress book targeted to developers, with advanced content that exploits the full functionality of the most popular CMS in the world. Fully updated to align with WordPress 4.1, this edition has updated examples with all new screenshots, and full exploration of additional tasks made possible by the latest tools and features. You will gain insight into real projects that currently use WordPress as an application framework, as well as the basic usage and functionality of the system from a developer's perspective. The book's key features include detailed information and real-world examples that illustrate the concepts and techniques at work, plus cod... [Read More] Secure Coding Best Practices
- ASIN: 1118987241
- ASIN: 1118987241
- ISBN: 1118987241
- Brand: Wrox
- Manufacturer: Wrox
-
Hacking: The Art of Exploitation, 2nd Edition
Hacking is the art of creative problem solving, whether that means finding an unconventional solution to a difficult problem or exploiting holes in sloppy programming. Many people call themselves hackers, but few have the strong technical foundation needed to really push the envelope.Rather than merely showing how to run existing exploits, author Jon Erickson explains how arcane hacking techniques actually work. To share the art and science of hacking in a way that is accessible to everyone, Hacking: The Art of Exploitation, 2nd Edition introduces the fundamentals of C programming from a hacker's perspective.The included LiveCD provides a complete Linux programming and debugging environment—all without modifying your current operating system. Use it to follow along with the book's exampl... [Read More] Secure Coding Best Practices
- ASIN: 1593271441
- UPC: 884870524442
- ASIN: 1593271441
- ISBN: 1593271441
- Brand: imusti
- Manufacturer: No Starch Press
-
THE HACKING STARTER KIT: An In-depth and Practical course for beginners to Ethical Hacking. Including detailed step-by-step guides and practical demonstrations.
Take on Ethical Hacking at Your Own Pace Without Having to go Through Plain Impractical Textbooks.What if you had a Hacking course tailored to your needs as a beginner with walkthroughs and visual examples? Imagine how that would speed up your learning process and would decrease your learning curve. Would such a guide help you to accomplish your short term and long term goals when it comes to Hacking? Well it did for thousands of students already! Let me Introduce you to Code Addicts, a platform that thrives on the passion of creating courses and informational products to help beginners and intermediate programmers to get to their goals. Code Addicts is built on people with extensive experience in the Computer Science field that share a passion for giving back. This time they have taken th... [Read More] Secure Coding Best Practices
- ASIN: B075J3BLS9
- ASIN: B075J3BLS9
-
WordPress for Beginners 2019: A Visual Step-by-Step Guide to Mastering WordPress (Webmaster Series Book 2)
Master WordPress using our step-by-step visual approach (over 330 screenshots). This book is a major new release for 2019, covering the latest version of WordPress.Building a beautiful, professional looking WordPress website (or a blog), is no longer the domain of computer geeks. WordPress makes it possible for anyone to create and run a website that looks great on any device - PC, Mac, tablet and phone. Whether you want to build a business site, an affiliate site, a hobby site or a blog, WordPress is a great choice.The primary goal of this book is to take anyone, even an absolute beginner, from zero to WordPress "guru" in a few short hours. Inside this book, veteran WordPress expert Andy Williams will start at the very beginning. You'll learn important topics like: • The two diff... [Read More] Secure Coding Best Practices
- ASIN: B07JH4BH7K
- ASIN: B07JH4BH7K
-
SQL: 2 Books In 1; Beginners And Intermediate Guide In SQL Programming
★ ★ Buy the Paperback version of this book, and get the Kindle eBOOK version for FREE★ ★BeginnerIf you own a company and have to keep track of a database with lots of information, or at least information that needs to stay secure, then SQL is the right option for you. This is a simple coding language that anyone can use and will often just require a few lines to get the work done. But with those few lines, you can write out a strong code that will help you to get, sort through, and create a database that works for you.This guidebook will take a look at all the different topics that you will need to learn to make SQL work for you. Some of the topics that we will discuss in this guidebook about the SQL language include:What is SQLWhy is it better than other database management langu... [Read More] Secure Coding Best Practices
- ASIN: B07JGP27BH
- ASIN: B07JGP27BH
-
Defensive Security Handbook : Best Practices for Securing Infrastructure
Despite the increase of high-profile hacks, record-breaking data leaks, and ransomware attacks, many organizations don't have the budget to establish or outsource an information security (InfoSec) program, forcing them to learn on the job. For companies obliged to improvise, this pragmatic guide provides a security-101 handbook with steps, tools, processes, and ideas to help you drive maximum-security improvement at little or no cost.Each chapter in this book provides step-by-step instructions for dealing with a specific issue, including breaches and disasters, compliance, network infrastructure and password management, vulnerability scanning, and penetration testing, among others. Network engineers, system administrators, and security professionals Secure Coding Best Practices Despite the increase of high-profile hacks, record-breaking data leaks, and ransomware attacks, many organizations don't have the budget to establish or outsource an information security (InfoSec) program, forcing them to learn on the job. For companies obliged to improvise, this pragmatic guide provides a security-101 handbook with steps, tools, processes, and ideas to help you drive maximum-security improvement at little or no cost.Each chapter in this book provides step-by-step instructions for dealing with a specific issue, including breaches and disasters, compliance, network infrastructure and password management, vulnerability scanning, and penetration testing, among others. Network engineers, system administrators, and security professionals
- UPC: 55479617
-
Perl Best Practices : Standards and Styles for Developing Maintainable Code
Many programmers code by instinct, relying on convenient habits or a "style" they picked up early on. They aren't conscious of all the choices they make, like how they format their source, the names they use for variables, or the kinds of loops they use. They're focused entirely on problems they're solving, solutions they're creating, and algorithms they're implementing. So they write code in the way that seems natural, that happens intuitively, and that feels good. But if you're serious about your profession, intuition isn't enough. Perl Best Practices author Damian Conway explains that rules, conventions, standards, and practices not Secure Coding Best Practices Many programmers code by instinct, relying on convenient habits or a "style" they picked up early on. They aren't conscious of all the choices they make, like how they format their source, the names they use for variables, or the kinds of loops they use. They're focused entirely on problems they're solving, solutions they're creating, and algorithms they're implementing. So they write code in the way that seems natural, that happens intuitively, and that feels good.But if you're serious about your profession, intuition isn't enough. Perl Best Practices author Damian Conway explains that rules, conventions, standards, and practices not only
- UPC: 3984532
- Rating: 5.0

-
JavaScript: Best Practices to Programming Code with JavaScript - eBook
Learn how to write effective and efficient JavaScript code for programming success and continue your progress towards JavaScript programming mastery!In this Definitive JavaScript Guide on Best Practices, you're about to discover how to...Code more efficiently for Better Performance and Results!Spot the Common JavaScript Mistakes - From mismatched quotes, bad line breaks, HTML conflicts and more!Apply Recommended JavaScript approaches - The DO's and DONT's of JavaScript programming that will help you code achieve its goals immensely!Use Comments and Logging – the proper way to use comments and logging approaches that readers would thank you for!... And much, much more!Added Benefits of Secure Coding Best Practices JavaScript: Best Practices to Programming Code with JavaScript - eBook
- UPC: 760976654
-
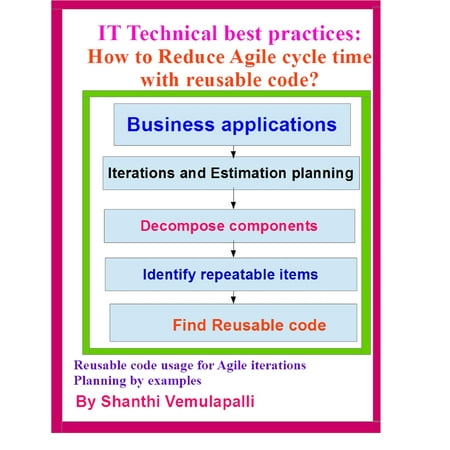
IT Technical best practices: How to Reduce Agile cycle time with reusable code? - eBook
In many Agile transformation sessions the Agile practitioners or savvy’s discuss more on the process related activities rather than elaborating on the technical or software engineering process steps to reduce the cycle time. At the same time prior to the Agile meetings, activity efforts need to be defined by the designers and the developers. Unless they identify the size of the reusable code components in the applications it is not worth for conducting the Release or Sprint planning meetings for planning of the iterations. Hence it is the moral responsibility of the technical teams to apply this kind of practices Secure Coding Best Practices IT Technical best practices: How to Reduce Agile cycle time with reusable code? - eBook
- UPC: 225671033
-
Java: Best Practices to Programming Code with Java - eBook
**Are you tired of constantly finding errors in your Java code? Fed up with not being able to understand what you have written, making it difficult to identify those errors? And how many times has your code been criticized by others for a lack of readability or for not being efficient? **In "Java: Best Practices to Programming Code with Java", the book information found here is designed to make things easier for you. This book will tell you the right way to lay out your code, why it should be done that way and show you several examples.You are about to learn:- Secure Coding Best Practices Java: Best Practices to Programming Code with Java - eBook
- UPC: 420349233
Secure Coding Best Practices
Computer systems are under siege 24 hours a day, day in and day out. The critical security infrastructure designed to protect those systems, won't: * Perimeter security won't protect you. * Netw... security,web security,hacking,program security,secure coding,secure code,app vulnerabilities
Secure Coding Techniques - CompTIA Security+ SY0-501 - 3.6
Security+ Training Course Index: http://professormesser.link/sy0501 Professor Messer’s Course Notes: http://professormesser.link/501cn Frequently Asked Questions: http://professormesser.link/faq - ... security+,sy0-501,certification,comptia,free,professor messer,code,secure,error handling,exceptio...
Secure Coding Best Practices
Learn why secure coding practices are important to reduce common programming errors that lead to vulnerabilities. Secure Coding,Cybersecurity
© 10Bestify.com - all rights reserved - Sitemap 10Bestify.com is a participant in the Amazon Services LLC Associates Program, an affiliate advertising program designed to provide a means for sites to earn advertising fees by advertising and linking to Amazon.com